Using aws-cli to authenticate to an External AWS Account configured with SSO
tldr;
We can't use aws-cli to authenticate via AWS SSO to an 'External AWS Account' ...
But I found out why 🙂
AWS Single Sign-On (AWS SSO) allows us to centrally manage single sign-on access to all of our AWS accounts
AWS SSO can also allow us to add 'External AWS Accounts'
A Stack Overflow post describes the process here: https://stackoverflow.com/questions/67703886/aws-sso-for-external-client-aws-accounts-not-in-an-organization-best-practices
When we add an External AWS account to our SSO, we have to add it as an 'Application'
We have to begin with how we first added the External AWS account to IAM Identity Center (formally AWS SSO console.aws.amazon.com/singlesignon/home)
Following the instructions to 'Add an External AWS account', our AWS SSO start page will look like this:
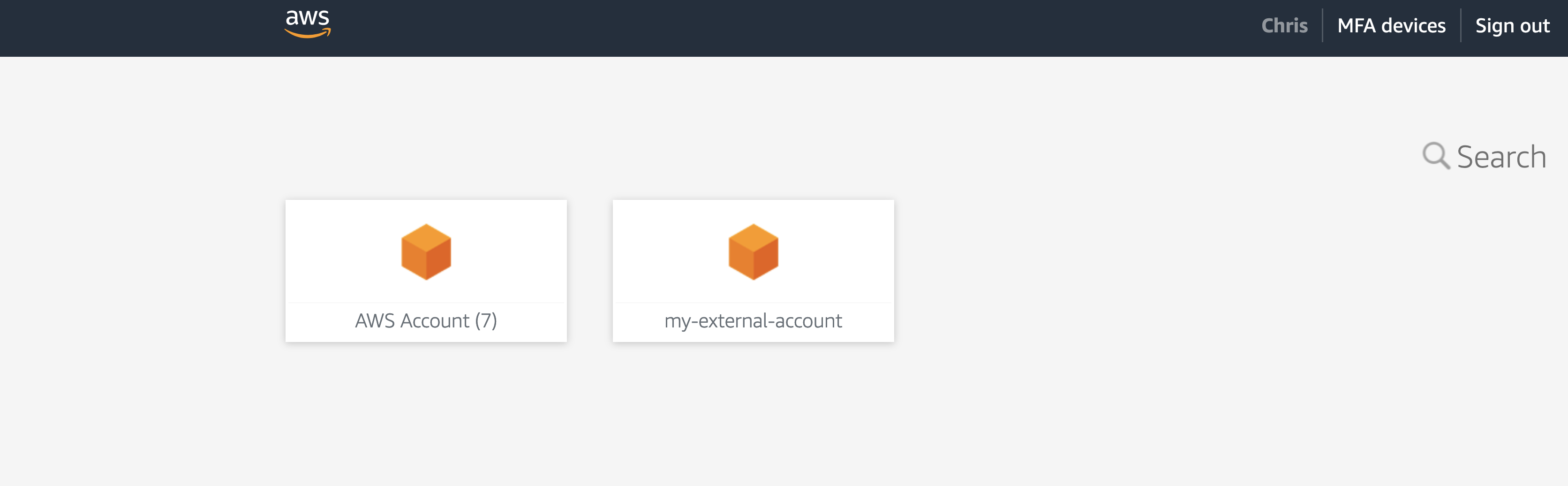
If we click on 'my-external-account' in the console, it will successfully assume a role and give us access to that AWS account
This is where the rabbit hole starts ...
Why can't we use AWS CLI to replicate this?
AWS SSO allows us to add 'Applications', one of which is an AWS account
They are authenticated via SAML
The confusion is, when we add an 'Application' pointing to an External AWS Account they appear as normal AWS accounts in the console
We only added the 'my-external-account' AWS account as an 'Application' - eg. a SAML compliant application
AWS do provide tutorial on how to get the SAML response, but it requires logging in via the console recording the network traffic ...
(https://www.youtube.com/watch?v=ACWRmFjG9V8)
Currently, AWS SSO cli doesn't provide a way to generate a SAML response required to authenticate with another AWS IDP
So how do we authenticate to the 'External AWS Account'?
We need to forget that we have added the External AWS account as an Application
However, remember the IAM Role we created in the External Account to allow the IDP
An AWS User will only escalate to the AWSReservedSSO group when using SSO to authenticate to an account within their AWS Organisation
Knowing this, we can modify the policy to allow the users within that group - eg. only user accounts that have logged in via SSO and are part of a group that have required permissions
Something like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<ext-account-id>:saml-provider/my-aws-provider"
},
"Action": "sts:AssumeRoleWithSAML",
"Condition": {
"StringEquals": {
"SAML:aud": "https://signin.aws.amazon.com/saml"
}
}
},
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<sso-account-id>:root"
},
"Action": "sts:AssumeRole",
"Condition": {
"ArnLike": {
"aws:PrincipalArn": "arn:aws:iam::<sso-account-id>:role/aws-reserved/sso.amazonaws.com/eu-west-2/AWSReservedSSO_<admin-role-name>s_*" }
}
]
}So now, we can use AWS SSO to log into the <sso-account-id> with the <admin-rolr-name> permission set, and then Assume the External Account role
 chris.qa
chris.qa